QUICK SUMMARY
Session Border Controllers (SBCs) in IMS architecture manage security, interoperability, and QoS, ensuring seamless and secure communication across network boundaries for high-quality multimedia services.
Session Border Controllers (SBCs) are pivotal in contemporary telecommunications, especially within the IP Multimedia Subsystem (IMS) architecture. SBCs are strategically positioned at the edges of networks to manage and control the ingress and egress of VoIP and multimedia traffic. This comprehensive guide delves into the core components, functionalities, and integration of SBCs within an IMS framework, providing insights into their critical role in contemporary telecommunications.
Limited-Time Offer on Our Comprehensive SBC Architecture Plans.
Understanding SBC Architecture
The SBC architecture is designed to handle signaling and media streams while providing robust security, quality of service (QoS), and session management capabilities. At its core, an SBC performs several vital functions:
- Security: SBCs protect the network from threats, including Denial of Service attacks, eavesdropping, and unauthorized access. They enforce security policies, provide encryption, and ensure that only legitimate traffic passes through the network boundaries.
- Interoperability: SBCs facilitate communication between different network protocols and devices. They perform protocol translation and media interworking, ensuring that diverse systems can seamlessly communicate with each other.
- Quality of Service (QoS): SBCs manage bandwidth allocation and prioritize traffic to ensure that high-priority communication, such as voice and video calls, receives the necessary resources for optimal performance. This is crucial in maintaining a consistent and high-quality user experience.
- Media and Signaling Control: SBCs handle both the media streams and signaling messages between endpoints. They manage session initiation, maintenance, and termination, ensuring robust and efficient communication sessions.
Understanding the logical and physical components of SBC architecture helps appreciate their importance and functionality in managing seamless and secure IP communications.
Core Functional Components of SBCs
Session Border Controllers offer a range of functionalities essential for the seamless operation of communication systems. Here’s an in-depth look at the core functional components of SBCs:
1. Signaling Plane Control
Signaling Plane Control manages communication session initiation, maintenance, and termination.
- Protocol Interworking: SBCs are equipped to handle a variety of signaling protocols used across different networks (e.g., SIP, H.323). It includes protocol translation capabilities, allowing seamless communication between devices and networks using different protocols.
- Session Control: Manages communication session setup, modification, and teardown. It ensures that sessions are established smoothly and modified or terminated as needed by network policies or user commands.
2. Media Plane Control
Media plane control implements security measures to protect media streams from eavesdropping and tampering.
- Media Transcoding: Converts media streams between different formats to ensure compatibility between other network devices or sectors. It is crucial when the communicating endpoints do not support the same media codecs.
- Media Security: Implements security measures such as encryption, decryption, and packet authentication to protect media streams from eavesdropping and tampering.
3. Transport and Network Layer Control
Transport and network layer control manages Network Address Translation (NAT) and supports Virtual Private Network (VPN) connections across shared or public networks.
- NAT Traversal: Manages Network Address Translation (NAT), allowing devices behind a NAT to locate and communicate with each other through an SBC.
- VPN Connectivity: Supports Virtual Private Network (VPN) connections, enhancing secure communications across shared or public networks.
4. Application Layer Functions
SBCs are equipped with application-level gateway firewalls that perform detailed inspections of the data passing through them. This allows for more sophisticated security measures and ensures that only authorized messages are allowed through the network.
- Application-Level Gateway (ALG): SBCs are equipped with application level gateway firewalls that perform detailed inspections of the data passing through them. This allows for more sophisticated security measures, such as detecting and preventing intrusion attempts, managing sessions more securely, and ensuring that only authorized messages are allowed through the network.
- Service Quality Management: Monitors and manages service quality by prioritizing traffic, controlling bandwidth, and implementing congestion avoidance techniques.
SBCs protect and enhance the efficiency of VoIP networks and pave the way for the scalable deployment of advanced communication solutions. Leveraging the core functional components of SBCs is vital for any organization looking to maximize the benefits of its IP communication infrastructure.
IMS Architecture
The IP Multimedia Subsystem (IMS) is a comprehensive architectural framework that delivers IP-based multimedia services. IMS enables the integration of voice, video, and data services over a unified IP network, providing a standardized approach for communication service providers. It is built on the Session Initiation Protocol (SIP) principles and leverages various standardized interfaces to ensure interoperability and scalability.
The IMS architecture comprises several key components, each playing a distinct role in managing multimedia services. These components include the Call Session Control Functions (CSCF), IMS Terminal, and the Border Gateway Function (BGF). Together, these components facilitate the seamless delivery of multimedia services across diverse network environments.
1. Call Session Control Function (CSCF)
The CSCF is a critical component in the IMS architecture, responsible for managing SIP signaling for session establishment, maintenance, and termination. There are three major types of CSCFs: Proxy-CSCF (P-CSCF), Interrogating-CSCF (I-CSCF), and Serving-CSCF (S-CSCF), each with specific roles in handling SIP messages and managing user sessions.
2. IMS Terminals
IMS terminals are endpoint devices that support IMS services, such as smartphones, VoIP phones, or multimedia applications on PCs. These terminals interact with the IMS network to provide users with voice, video, and data services.
Key Functions of IMS Terminals
Here are some of the significant IMS terminals given below:
- Voice Services
- Voice over LTE (VoLTE): IMS terminals support VoLTE, which provides high-quality voice calls over 4G LTE networks.
- HD Voice: Enhanced voice quality for more explicit and more natural-sounding calls.
- Video Services
- Video Calling: Enables real-time video communication between users, providing a richer communication experience.
- Video Conferencing: Supports multi-party video conferences for personal and business communication.
- Data Services
- Rich Communication Services (RCS): Includes features like group chat, file transfer, and presence information, enhancing traditional SMS and MMS services.
- Instant Messaging: Real-time text messaging with additional features like media sharing and read receipts.
3. Border Gateway Function (BGF)
The Border Gateway Function is another crucial aspect of SBC architecture. It manages the media streams that traverse the borders of different network segments. BGF is responsible for tasks such as media transcoding, ensuring compatibility across network boundaries, and performing rate adaptation and media encryption.
- Media Transcoding: The BGF converts media streams from one format to another. It is essential for ensuring compatibility between network devices or sectors, notably when the communicating endpoints do not support the same media codecs.
- Compatibility Across Network Boundaries: BGF ensures that media streams can traverse various network boundaries without issues. It manages different protocols and codecs to maintain compatibility, allowing seamless communication between disparate network segments.
- Rate Adaptation: BGF performs rate adaptation to adjust the media stream’s bit rate according to network conditions. This helps maintain the quality of the media stream even when there are variations in network bandwidth.
- Media Encryption: BGF implements media encryption to protect the media streams from eavesdropping and tampering. By encrypting the media packets, it ensures that the communication remains secure and private across network boundaries.
The Border Gateway Function is essential for managing and securing media streams as they pass through different network segments, ensuring compatibility, maintaining quality, and providing robust security measures.
4. Application Level Gateway Firewall
An Application Level Gateway Firewall manages and controls application-layer traffic between networks. It inspects and filters traffic based on the content and protocols used by applications, ensuring that only authorized communication passes through.
Key Functions of Application Level Gateway Firewall
Here are some of the crucial functions of an Application Level Gateway Firewall:
- Deep Packet Inspection (DPI): The ALG Firewall performs deep packet inspection, analyzing data packets beyond the basic header information. It inspects each packet’s payload to understand the nature of the traffic. Examining the content of the packets can block some malicious activities, such as malware, viruses, and unauthorized access attempts.
- Session Management: The firewall manages sessions by tracking the state of active connections. It can monitor the session lifecycle, ensuring that each session adheres to the security policies. It helps prevent session hijacking and ensures that only authorized users can maintain active sessions.
- Traffic Monitoring and Logging: The firewall continuously monitors traffic and maintains activity logs. It includes recording details about who accessed what, when, and from where. Traffic monitoring and logging are crucial for auditing, compliance, and forensic analysis in case of a security incident.
- Application-Level Controls: The firewall enforces security controls at the application level, such as requiring user authentication before accessing specific applications or services. It ensures that only some authorized users can access sensitive applications, providing an additional layer of security.
It protects against a wide range of security threats by ensuring that only authorized and legitimate application traffic passes through.
5. 3GPP (3rd Generation Partnership Project) Architecture Perspective
3 GPP provides a framework for standardizing protocols and functionalities for mobile and network communications, including IMS.
Role of 3GPP in IMS Standardization
3GPP is the primary organization responsible for developing and maintaining the standards for IMS architecture. 3GPP’s specifications ensure that IMS components are interoperable and adhere to a common framework, essential for global compatibility and efficient network operation.
3GPP’s standardization efforts cover various aspects of IMS, including:
- Network Architecture: Defining the structure and components of IMS networks.
- Protocols: Standardizing the signaling and communication protocols used within IMS.
- Security: Establishing security mechanisms and best practices to protect IMS networks.
- Interoperability: Ensuring that IMS components from different vendors can work together seamlessly.
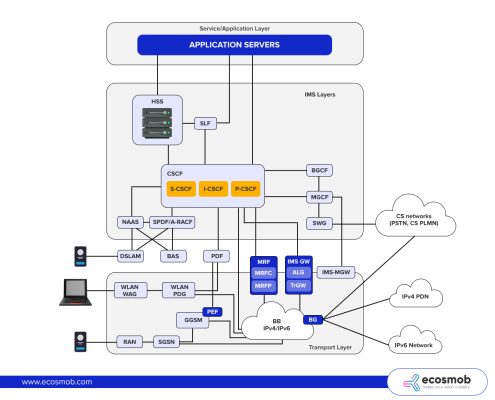
3GPP’s standards are continually evolving to incorporate new technologies and address emerging challenges, making IMS a robust and future-proof framework for multimedia communication.
Call Session Control Function (CSCF)
CSCF is a fundamental component in the IMS architecture, responsible for managing SIP signaling and handling multimedia sessions.
Types of CSCF
CSCF is crucial for managing call sessions and various communication services in an IMS network. There are three main types of CSCF, each serving distinct roles:
1. Proxy Call Session Control Function (P-CSCF)
The P-CSCF is the original point of contact for IMS terminals. It is responsible for forwarding SIP messages between the IMS terminal and the IMS core network. The P-CSCF also applies security policies, manages QoS, and performs NAT traversal. It ensures that signaling messages are routed correctly and securely. It interacts with the IMS terminal during registration and session establishment, enforcing security and QoS policies.
- Session Initiation: Handling the initial signaling messages from the UE and forwarding them to the appropriate CSCF.
- Security: Implementing security policies, including user authentication and integrity protection of the signaling messages.
- NAT Traversal: Managing Network Address Translation (NAT) traversal to ensure seamless communication between devices behind NATs and the IMS network.
2. Interrogating Call Session Control Function (I-CSCF)
The I-CSCF acts as the contact point within an operator’s network for all incoming connections destined for a subscriber. It queries the Home Subscriber Server (HSS) to obtain user location information and routes SIP messages to the appropriate S-CSCF. The I-CSCF plays a crucial role in routing and registration processes. It ensures that incoming SIP messages are directed to the correct S-CSCF based on the user’s location and registration status.
- Routing: Determining the appropriate S-CSCF for a session based on user information and network policies.
- Interconnection: Facilitating communication between operators’ networks by acting as a gateway.
- Network Discovery: Querying the Home Subscriber Server (HSS) to locate the user’s S-CSCF and route the signaling messages accordingly.
3. Serving Call Session Control Function (S-CSCF)
The S-CSCF is central to session control, managing user registration, authentication, and session establishment. It maintains the session state and ensures that all SIP signaling is handled correctly. The S-CSCF handles user authentication, registration, and session management. It ensures that multimedia sessions are established and maintained effectively, providing each subscriber with the contracted features and services.
- Session Management: Establishing, modifying, and terminating call sessions. It maintains the session state and ensures proper signaling flow.
- Service Invocation: Triggering the execution of various services and applications based on user profiles and session parameters.
- Registration: Handling user registration by communicating with the HSS to authenticate and authorize users.
Together, these CSCF components form the backbone of the IMS network, enabling advanced communication services with high reliability, security, and quality. Understanding their distinct functionalities is crucial for leveraging IMS’s full potential in delivering next-generation multimedia services.
Border Gateway Function (BGF)
The Border Gateway Function (BGF) is an essential component in the IMS architecture, responsible for managing the secure traversal of signaling and media streams across different network domains. The Border Gateway Function works closely with the SBC to enforce security policies, manage NAT, perform firewall traversal, and ensure media encryption.
Importance in IMS Architecture
In the IMS architecture, the Border Gateway Function ensures that media streams can traverse NATs and firewalls securely, protecting against potential threats such as DoS attacks. The Function also helps maintain QoS by managing media routing and applying necessary policies to ensure efficient and reliable communication. These functions collectively ensure that signaling within the IMS network is routed and controlled efficiently, enhancing the network’s overall performance.
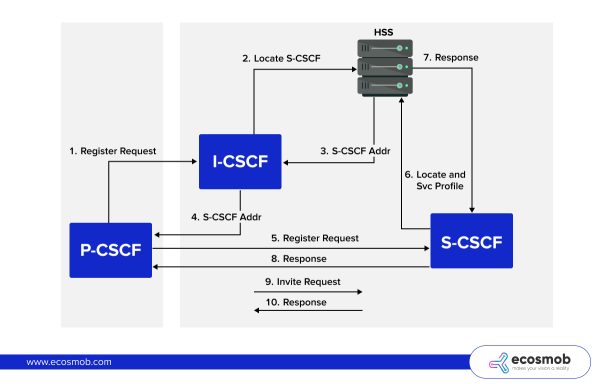
The signaling flow between components in an IP Multimedia Subsystem (IMS) network during the registration and Session Initiation Processes is given here in the image. Here’s a step-by-step breakdown:
- Register Request (P-CSCF): The process begins with a device sending a registration request to the Proxy-Call Session Control Function (P-CSCF), which acts as the initial contact point within the IMS network for SIP (Session Initiation Protocol) clients.
- Locate S-CSCF (I-CSCF): The P-CSCF forwards this registration request to the Interrogating-CSCF (I-CSCF). The I-CSCF role is to query the Home Subscriber Server (HSS) to determine which Serving-CSCF (S-CSCF) should handle the request.
- S-CSCF Address (HSS): The HSS provides the address of the appropriate S-CSCF based on the user’s profile and current state.
- S-CSCF Addr (I-CSCF to P-CSCF): The I-CSCF forwards the address of the determined S-CSCF back to the P-CSCF.
- Register Request (P-CSCF to S-CSCF): The P-CSCF then sends the registration request directly to the designated S-CSCF.
- Locate and Svc Profile (S-CSCF): Upon receiving the registration, the S-CSCF retrieves the user’s service profile from the HSS to apply any services or routing policies specific to that user.
- Response (HSS to S-CSCF): The HSS sends a response to the S-CSCF confirming the retrieval and successful application of the service profile.
- Response (S-CSCF to P-CSCF): The S-CSCF responds to the P-CSCF, indicating the registration has been successfully processed.
- Invite Request (P-CSCF to S-CSCF): Following registration, if a session (like a voice call) needs to be initiated, the P-CSCF sends an INVITE request to the S-CSCF.
- Response (S-CSCF to P-CSCF): The S-CSCF processes the INVITE request and sends a corresponding response back to the P-CSCF, which will manage the session’s setup with the originating device.
This flow ensures that the IMS network can efficiently manage registrations and session setups, applying user-specific services and routing calls correctly based on the network’s real-time conditions and configurations.
Application Level Gateway Firewall
An Application-Level Gateway (ALG) Firewall is a type of firewall that manages and controls application-layer traffic between networks. Unlike traditional firewalls, which operate at lower layers of the OSI model, ALGs inspect and filter traffic based on the content and protocols used by applications.
Importance in Securing Communication
In IMS, the ALG Firewall is crucial in securing communication by inspecting SIP messages and applying security policies. It ensures that only authorized communication passes through the network boundaries, protecting against unauthorized access and potential threats.
IMS Terminal
An IMS terminal is any endpoint device that supports IMS services, such as smartphones, VoIP phones, or multimedia applications on PCs. These terminals can register with the IMS network through the P-CSCF, enabling access to a variety of multimedia services.
Role in IMS Networks
IMS terminals play a crucial role in delivering end-user services, including voice and video calls, messaging, and presence information. They interact with CSCFs to establish and maintain multimedia sessions, ensuring a seamless user experience.
Interrogating Call Session Control Function (I-CSCF)
Interrogating Call Session Control Function (I-CSCF) is a significant point within an operator’s network for all connections destined for a subscriber. It queries the Home Subscriber Server (HSS) to retrieve user location information and plays a crucial role in routing and registration processes.
Importance in Routing and Registration
I-CSCF is essential for efficient session management. It ensures that SIP messages are correctly routed to the appropriate S-CSCF based on the user’s location and registration status. This function helps maintain the overall integrity and efficiency of the IMS network.
Integration of SBC in IMS Architecture
SBCs are strategically placed at the network borders to manage and control the ingress and egress of signaling and media traffic. They interact with various IMS components to enforce security, QoS, and interoperability policies. The following diagram illustrates the placement of SBCs within an IMS architecture:
Interaction Between SBC and Other IMS Components
The interaction between SBCs and other IMS components is critical for maintaining multimedia services’ quality, security, and efficiency. Here’s how SBCs interact with various IMS components:
-
SBC and P-CSCF
-
-
- The SBC works with the P-CSCF to manage signaling and apply security policies.
- Ensures that media streams are routed securely through the network.
-
-
SBC and I-CSCF
-
-
- Collaborates with the I-CSCF to query user location information and route SIP messages.
- Enhances the efficiency of session management.
-
-
SBC and S-CSCF
-
-
- Manages session control and user authentication in conjunction with the S-CSCF.
- Ensures that multimedia sessions are established and maintained effectively.
-
-
SBC and BGF
-
- Ensures secure media traversal across network boundaries.
- Applies NAT, firewall traversal, and media encryption policies.
By effectively interacting with other IMS components, SBCs play a vital role in maintaining secure, efficient, high-quality multimedia communications within IMS networks.
Implementing SBC in an IMS Network
Implementing a Session Border Controller (SBC) in an IP Multimedia Subsystem (IMS) network is essential for ensuring secure, efficient, and high-quality multimedia communications. Here’s a step-by-step guide on how to implement an SBC in an IMS network:
1. Assessment and Planning
- Evaluate Existing Infrastructure: Assess the current network infrastructure to identify the components that must be integrated with the SBC. It includes understanding the existing protocols, devices, and security policies.
- Identify Requirements: Determine the specific requirements for SBC implementation, including security, QoS, and interoperability. It involves defining the KPIs and objectives for the SBC deployment.
2. Design and Configuration
- Design SBC Architecture: Create a detailed design of the SBC architecture, considering its placement and interaction with IMS components. It includes defining the network topology and identifying the interfaces and protocols.
- Configure SBC Policies: Configure the SBC with the necessary security, NAT traversal, firewall management, and QoS policies. It involves setting up rules for traffic filtering, encryption, and prioritization.
3. Integration and Testing
- Integrate SBC into IMS Network: Integrate the SBC with the existing IMS network components, such as CSCFs, BGFs, and HSS. It involves connecting the SBC to the network and ensuring it can communicate with other IMS elements.
- Conduct Thorough Testing: Perform comprehensive testing to ensure that the SBC operates correctly and meets the defined requirements. It includes testing for interoperability, security, and QoS.
4. Deployment and Monitoring
- Deploy SBC in Live Environment: Deploy the SBC in the live network environment, ensuring it is fully operational and integrated with other IMS components. This involves monitoring the deployment process and addressing any issues that arise.
- Monitor Performance: Continuously monitor the SBC’s performance to ensure optimal operation. It includes tracking KPIs, analyzing traffic patterns, and adjusting policies to maintain security and QoS.
Once the SBC is integrated and tested, it is deployed in the live environment with continuous monitoring to maintain optimal operation. By adhering to these effective steps, organizations can effectively enhance their IMS networks, ensuring robust, secure, and high-performance multimedia communications.
Deployment Models
Implementing a Session Border Controller (SBC) can be done through various deployment models, each suited to different network environments and organizational needs. Here’s a detailed explanation of the primary SBC deployment models:
Standalone Deployment
In this model, the SBC is deployed as a dedicated appliance or virtual instance that operates independently of other network devices.
Major Advantages
Here are some of the benefits given below:
- High Performance: By being dedicated, it offers high performance, handling large volumes of traffic with low latency.
- Reliability: Ensures reliable operation, specifically designed and optimized for SBC functions.
- Security: Enhanced security through isolation from other network functions.
Integrated Deployment
The SBC is integrated with other network elements, such as routers, gateways, or Unified Communications (UC) platforms.
Key Advantages
Here are some of the major advantages given below:
- Simplified Architecture: Reduces the complexity of the network architecture by combining multiple functions into a single device.
- Cost Efficiency: Lowers the number of devices to manage, which can reduce both capital and operational expenditures.
- Streamlined Management: Simplifies network management and maintenance through centralized control.
Cloud-Based Deployment
The SBC is deployed in public or private cloud environments, leveraging cloud infrastructure for its operations.
Key Advantages
Here are some of the major benefits given below:
- Elastic Scalability: Easily scales up or down based on demand, accommodating fluctuating traffic volumes.
- Reduced CapEx: Lowers capital expenditures by eliminating the need for physical hardware investments.
- Simplified Management: Centralized management and maintenance through cloud service providers.
Hybrid Deployment
This model combines on-premises and cloud-based SBCs, blending both deployment strategies.
Major Advantages
Here are some of the key benefits given below:
- Local Control: Provides the ability to maintain control over critical functions and data locally.
- Cloud Scalability: Utilizes cloud resources for scaling and redundancy, ensuring business continuity.
- Flexibility: Offers the best of both worlds, balancing performance, control, and scalability.
Choosing the right SBC deployment model depends on the needs and goals of the organization. By understanding the advantages of each model, organizations can select the most suitable SBC deployment strategy to enhance their IMS network operations.
Challenges and the Ways to Overcome SBC in an IMS Network
The Session Border Controller (SBC) plays a crucial role in managing and securing IP Multimedia Subsystem (IMS) networks. However, deploying and maintaining SBCs in an IMS environment comes with several challenges. Here’s a look at these challenges and effective strategies to overcome them:
1. Security Concerns
The major concern is ensuring robust security to protect against potential threats such as DoS attacks and unauthorized access, which is a critical challenge. We can overcome this challenge by Implementing robust encryption and authentication mechanisms, regularly updating security policies, and conducting periodic security audits.
2. Interoperability Issues
The challenge is to ensure compatibility with various network protocols and devices from different vendors. The solution is to conduct thorough interoperability testing, use standardized interfaces and protocols, and collaborate with vendors to address compatibility issues.
3. Quality of Service (QoS)
Maintaining high-quality communication for critical services such as voice and video calls is challenging. To overcome it, Implement traffic shaping and bandwidth management policies, prioritize essential traffic, and monitor network performance to identify and address QoS issues.
Addressing the challenges associated with SBCs in an IMS network requires a proactive and strategic approach. Network administrators can overcome these challenges by implementing industry best practices, leveraging advanced technologies, ensuring robust security measures, and ensuring a reliable and secure IMS environment.
Future Trends and Evolution of SBC and IMS Networks
These systems must adapt as technology progresses to meet new demands and challenges. Here are the future trends and evolution of SBC and IMS networks, focusing on emerging technologies, 5G integration, cloud-based solutions, and future standards and innovations.
Emerging Technologies in SBC and IMS Networks
Emerging technologies significantly influence the evolution of Session Border Controllers within IP Multimedia Subsystem (IMS) networks.
1. 5G Integration
Integrating 5G technology with IMS networks will enhance the capabilities of SBCs, enabling them to handle higher bandwidth and lower latency applications. SBCs will play a crucial role in managing and securing 5G communication, ensuring that the advanced features of 5G networks are fully utilized.
2. Cloud-Based SBC Solutions
The adoption of cloud-based SBC solutions is increasing, providing greater scalability and flexibility. The major impact is that Cloud-based SBCs offer improved integration with cloud-native IMS components, allowing for more efficient and cost-effective deployment and management.
Future Standards and Innovations
Advancements in security protocols, interoperability enhancements, and scalable performance architectures are shaping the future of session border controllers (SBCs) and IP multimedia subsystem (IMS) networks. These innovations can handle increasing traffic demands, ensuring reliable and efficient network operations.
1. Enhanced Security Protocols
Developing advanced security protocols is essential to protect IMS networks as cyber threats continue to evolve. Future SBCs will incorporate more sophisticated encryption, authentication, and access control mechanisms to ensure robust security.
2. Interoperability Enhancements
Standardization efforts will continue to improve interoperability between network protocols and devices. Innovations in protocol translation and media interworking will enable seamless communication across diverse network environments.
3. Scalability and Performance
The demand for scalable and high-performance SBC solutions will drive the development of new technologies and architectures. SBCs will leverage multi-core processing, distributed architectures, and cloud-based technologies to handle increasing traffic and complexity. The future of SBC and IMS networks is poised for significant transformation driven by technological advancements and evolving communication needs.
Wrapping Up
Session Border Controllers (SBCs) are integral to the success of IP Multimedia Subsystem networks, ensuring secure, reliable, and high-quality communication. Understanding the architecture and interaction of Ecosmob SBCs with other IMS components is crucial for implementing and managing modern telecommunications networks. With the continuous evolution of standards and technologies, SBCs will remain vital in delivering advanced multimedia services.
This comprehensive guide provides an SBC architecture overview within IMS networks, covering key components, implementation steps, and future trends. By leveraging the insights presented here, Ecosmob experts can effectively design, deploy, and manage SBCs to meet the demands of modern communication networks. Feel free to reach out to us at any time. Our experts are always here to assist you.
Transform Your VoIP Security with Our Cutting-Edge SBC Solutions
FAQs
What is an SBC architecture?
The SBC architecture refers to the structural design of Session Border Controllers (SBCs), which manage and secure VoIP and multimedia communication sessions across IP networks.
What role does the IMS terminal play in the SBC architecture?
The IMS terminal is an endpoint device in the IP Multimedia Subsystem that supports various multimedia services. It interacts with the SBC to establish and manage communication sessions, ensuring compatibility and security.
What is an application-level gateway firewall, and why is it important in SBC architecture?
An application-level gateway firewall inspects and filters application-specific data streams to enhance security. In SBC architecture, it prevents unauthorized access and protects against threats like DoS attacks.
How does the IP Multimedia Subsystem (IMS) integrate with SBC architecture?
The IMS framework integrates with SBC architecture to provide comprehensive multimedia services over IP networks. The SBC ensures secure and efficient management of signaling and media between the IMS components and external networks.
What is the significance of the 3GPP standards in SBC architecture?
The 3GPP standards define the technical specifications for mobile and IP communication systems, including SBC architecture. Adherence to these standards ensures interoperability and seamless communication across different networks and devices.







![SIP Protocol [SIP Signalling]](https://a4f8b050.delivery.rocketcdn.me/wp-content/uploads/2024/12/Blog-79.jpg)