QUICK SUMMARY
Kubernetes makes service discovery easy, but handling external traffic isn’t always straightforward. Ingress Controllers in Kubernetes fix that by managing how requests enter your cluster and get routed internally. This guide breaks down what they are, how they work, when to use them, and the most reliable options for 2025, including Ecosmob’s SIP-specific controller for VoIP and telecom!
Kubernetes makes scaling services easy. But exposing them to the outside world? That’s where it gets messy.
Most applications don’t just run one backend. You’re likely hosting multiple microservices; each on its own port, each needing external access. Without a strategy, this leads to a pile of Load Balancers, messy NodePorts, and unnecessary cloud costs.
That’s why Ingress Controllers exist—to centralize routing, reduce surface area, and manage external traffic with precision.
Let’s break it all down.
🔒What Is an Ingress in Kubernetes?
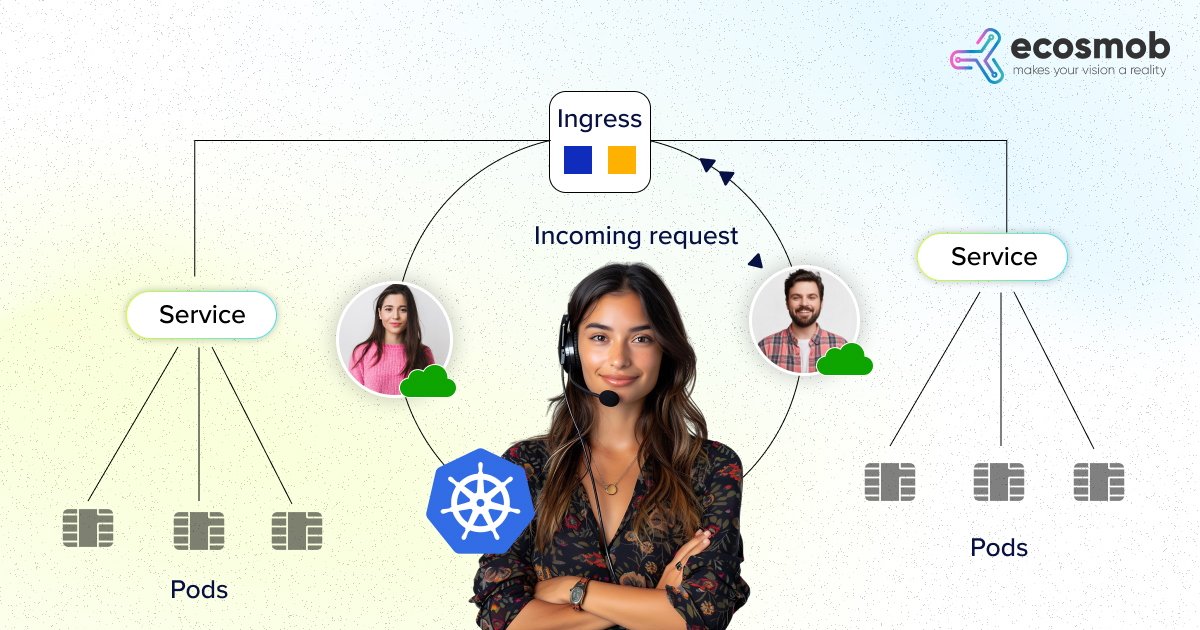
In Kubernetes, an Ingress is a set of rules that define how external traffic reaches services running inside the cluster. It doesn’t handle the traffic itself; it just tells Kubernetes what should happen when someone visits your application through a specific URL or domain.
Think of it as a traffic map for your cluster. You tell it things like:
- “All requests to myapp.com/api should go to the API service.”
- “All requests to myapp.com/dashboard should go to the frontend service.”
- “Only allow HTTPS traffic.”
But here’s the important part: Ingress rules are just instructions. They need a controller to carry them out.
Hacked together SIP routing wasting your time? We have THE solution to give you control, automation, and peace of mind.
❓What Is an Ingress Controller in Kubernetes?
An Ingress Controller is the component that reads your Ingress rules and enforces them. It watches the Kubernetes API for any new or updated Ingress resources and then updates its internal configuration to route incoming traffic accordingly.
You can think of Ingress as a set of directions, and the Ingress Controller as the driver that follows those directions.
It’s what actually:
- Accepts the request from the outside world
- Checks if it matches any of your rules
- Forwards it to the correct service running in the cluster.
Without an Ingress Controller, your Ingress rules won’t work at all.
✍️ How Does an Ingress Controller Work?
Let’s walk through a simplified flow:
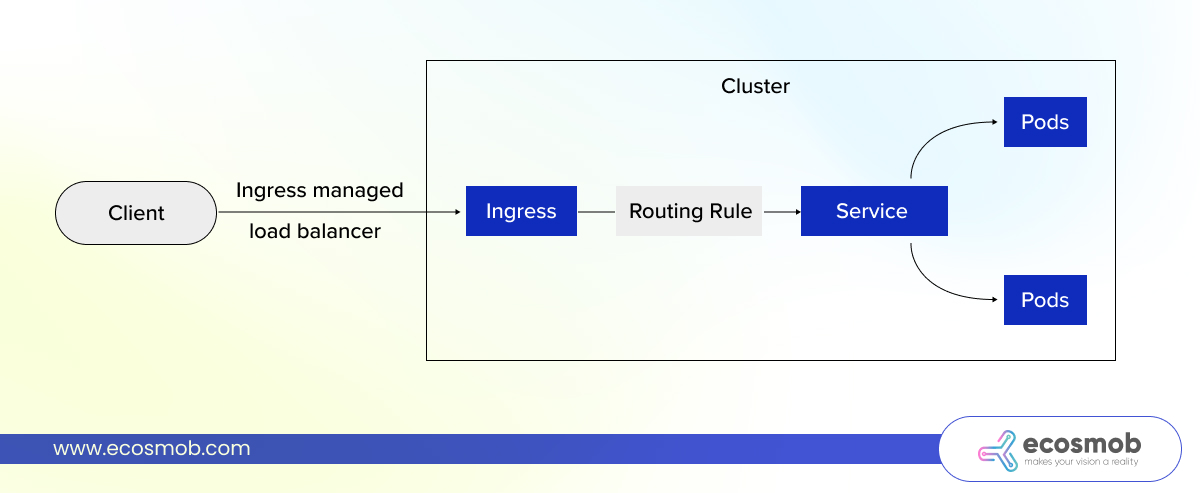
- A client sends an HTTPS request to your public Load Balancer IP.
- Then it is forwarded to the Ingress Controller running inside your cluster.
- The Ingress Controller looks up its internal routing table, which is built from your Ingress YAMLs.
- Based on the hostname and path, it routes traffic to the correct internal Kubernetes service.
- The request is then sent to the backend Pod through the Kubernetes Service.
🔑 Key Capabilities:
- TLS termination (end SSL at the ingress point)
- Path-based routing (e.g., /api to service A, /admin to service B)
- Rate limiting and IP filtering
- Automatic re-routing during pod failures
And because it runs as a pod inside your cluster, it automatically adapts to service updates, new deployments, and scale-ups.
 👉 How to Install an Ingress Controller in Kubernetes?
👉 How to Install an Ingress Controller in Kubernetes?
Installing an Ingress Controller is your first step to managing external traffic intelligently. While the process varies slightly depending on the controller you choose, the most common way is via Helm or kubectl.
Let’s walk through installing the NGINX Ingress Controller (one of the most widely used and beginner-friendly options).
☛ Step-by-Step: Install NGINX Ingress Controller using Helm
💧Add the Helm repo
helm repo add ingress-nginx https://kubernetes.github.io/ingress-nginx
helm repo update
💧Install the Ingress Controller
helm install ingress-nginx ingress-nginx/ingress-nginx \
–namespace ingress-nginx \
–create-namespace
💧Check if the pods are running
kubectl get pods -n ingress-nginx
💧Check the external IP (for cloud clusters)
kubectl get svc -n ingress-nginx
Now you can create an Ingress resource (YAML) to define routing rules.
☛ Example: Ingress YAML for Routing Traffic
Once your Ingress Controller is installed, you define how traffic should be routed using an Ingress resource. Here’s a simple example:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: app-ingress
annotations:
nginx.ingress.kubernetes.io/rewrite-target: /
spec:
rules:
– host: myapp.example.com
http:
paths:
– path: /api
pathType: Prefix
backend:
service:
name: api-service
port:
number: 80
– path: /web
pathType: Prefix
backend:
service:
name: frontend-service
port:
number: 80
What This Does:
- Traffic that goes to myapp.example.com/api will be forwarded to the api-service running inside your cluster.
- Traffic that goes to myapp.example.com/web will be sent to the frontend-service.
- Both routes are handled through a single LoadBalancer and one Ingress Controller.
This is how Ingress helps you reduce complexity and route multiple services through a single, smart entry point.
☑️ Want to Use a Cloud-Specific Controller?
- On AWS: Use the AWS ALB Ingress Controller, which integrates with native AWS Load Balancers.
- On Azure: Use the AGIC (Application Gateway Ingress Controller) for deeper Azure integration.
Each cloud-native controller has its own setup process, often involving IAM roles, annotations, and cloud-specific tooling.
Scaling Ingress in Kubernetes a headache? Our platform solves it—seamlessly.
🚦How Does an Ingress Controller Compare to Other Kubernetes Traffic Options?
In Kubernetes, there are four main ways to expose your services to the outside world:
- ClusterIP: Default type, only accessible inside the cluster
- NodePort: Opens a fixed port on each node’s IP
- LoadBalancer: Provisions a public cloud load balancer per service
- Ingress + Ingress Controller: Routes traffic to multiple services through one LoadBalancer and a set of smart rules
Let’s simplify the decision-making:
| Option | External Access | Best For | Downsides |
| ClusterIP | ❌ | Internal-only microservices that talk to each other | Cannot be accessed externally |
| NodePort | ✅
(via node’s IP + port) |
Simple dev/test scenarios with minimal setup | Fixed ports, limited flexibility |
| LoadBalancer | ✅
(via external IP) |
Exposing a single service in cloud environments | Expensive and inefficient for many services |
| Ingress Controller | ✅
(via single entry point) |
Centralizing access to multiple services | Requires setup, rules configuration |
In short:
- Use ClusterIP for internal traffic.
- Use NodePort for basic testing.
- Use LoadBalancer for simple public-facing services.
- Use Ingress Controller when you want a scalable, efficient, and centralized way to handle external traffic for multiple services.
Struggling with VoIP routing in Kubernetes? Let us simplify it for you—reliably and at scale.
Real-World Use Cases for Ingress Controllers
Here’s how Ingress Controllers simplify real business scenarios:
❑ Hosting Multiple Web Apps Under One Domain
You’re running:
- A marketing site at example.com
- A dashboard at example.com/dashboard
- An API backend at example.com/api
Rather than using three Load Balancers (one per service), you use a single Ingress Controller to handle routing, all through one domain and one IP address.
❑ Secure Access with HTTPS and TLS Termination
You want to serve everything over HTTPS. Instead of configuring SSL individually for every service, the Ingress Controller handles TLS termination at the edge and routes traffic securely inside the cluster.
❑ Cost Control in the Cloud
Cloud Load Balancers cost money (often per service). With an Ingress Controller, you can expose dozens of services using one Load Balancer, significantly reducing operational costs.
❑ Simplifying DevOps Workflows
Your CI/CD pipeline can update Ingress rules (not the entire infrastructure). Want to deploy a new version of your app under /v2? Just update the Ingress. No Load Balancer or DNS updates needed.
[Also, Watch our On-Demand Webinar on Mastering DevOps and Kubernetes Synergy.]
✅ Types of Ingress Controllers for Kubernetes
There’s no one-size-fits-all Ingress Controller. What may be the best Ingress Controller for Kubernetes in one scenario may not be in another.
The right one depends on your protocols, performance needs, and environment. Here are some of the most widely used ones in 2025:
❑ NGINX Ingress Controller
The most popular Kubernetes-native Ingress Controller, backed by the Kubernetes community.
- Why use it: It’s stable, customizable, and great for HTTP/S workloads.
- Use case: Ideal for production environments that need SSL, host/path routing, and good community support.
- Not ideal for: SIP or non-HTTP protocols.
❑ Traefik
A modern, dynamic Ingress Controller built for cloud-native stacks.
- Why use it: Automatic TLS via Let’s Encrypt, real-time service discovery, dashboard, and built-in metrics.
- Use case: Great for microservice-heavy environments and DevOps teams that want fast automation.
- Not ideal for: High-load traffic or fine-grained L7 routing complexity.
❑ HAProxy Ingress
Built on the HAProxy load balancer, known for low latency and high performance.
- Why use it: Offers deep control over L7 policies, traffic shaping, and connection limits.
- Use case: Enterprises and fintech apps that need strict performance control.
- Not ideal for: Teams without HAProxy experience—it has a learning curve.
❑ Kong Ingress Controller
A hybrid Ingress/API Gateway solution built on top of NGINX.
- Why use it: Adds features like rate limiting, JWT auth, and developer portals.
- Use case: API-first products that want both Ingress and API gateway functionality.
- Not ideal for: Simple apps that don’t need API management features.
❑ AWS ALB Ingress Controller
The AWS Kubernetes Ingress Controller provisions native AWS Application Load Balancers for Kubernetes.
- Why use it: Ties directly into IAM, WAF, CloudWatch, and AWS SSL.
- Use case: Kubernetes on EKS, where you want AWS-native integration and no extra pods.
- Not ideal for: Multi-cloud deployments—this only works inside AWS.
❑ Azure Application Gateway Ingress Controller (AGIC)
Azure’s native controller for Kubernetes clusters using AKS.
- Why use it: Tight integration with Azure networking, autoscaling, and firewall policies.
- Use case: Enterprises building on Azure looking for low-ops management.
- Not ideal for: Non-Azure workloads or cross-cloud deployments.
Ecosmob SIP Ingress Controller (Purpose-Built for VoIP and Real-Time Traffic)
Most Ingress Controllers were built for HTTP. But SIP? That’s a different protocol altogether.
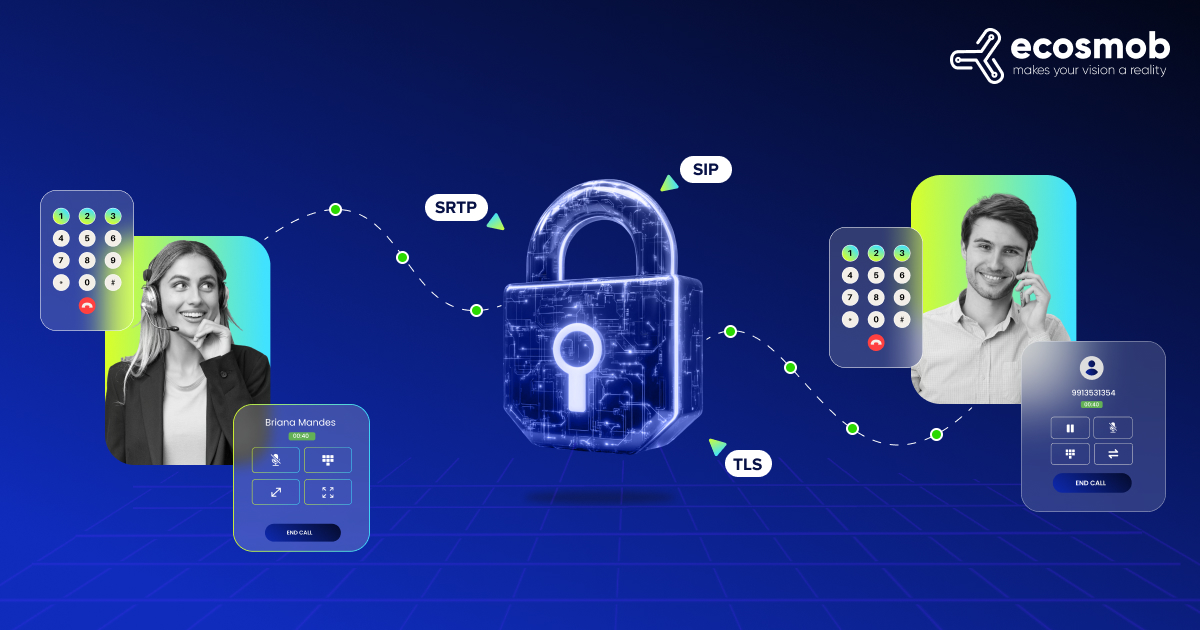
SIP isn’t stateless. It doesn’t use standard ports. It negotiates media on the fly and needs deep session awareness. That’s why traditional Ingress Controllers break when handling VoIP workloads.
Ecosmob’s SIP Ingress Controller changes that.
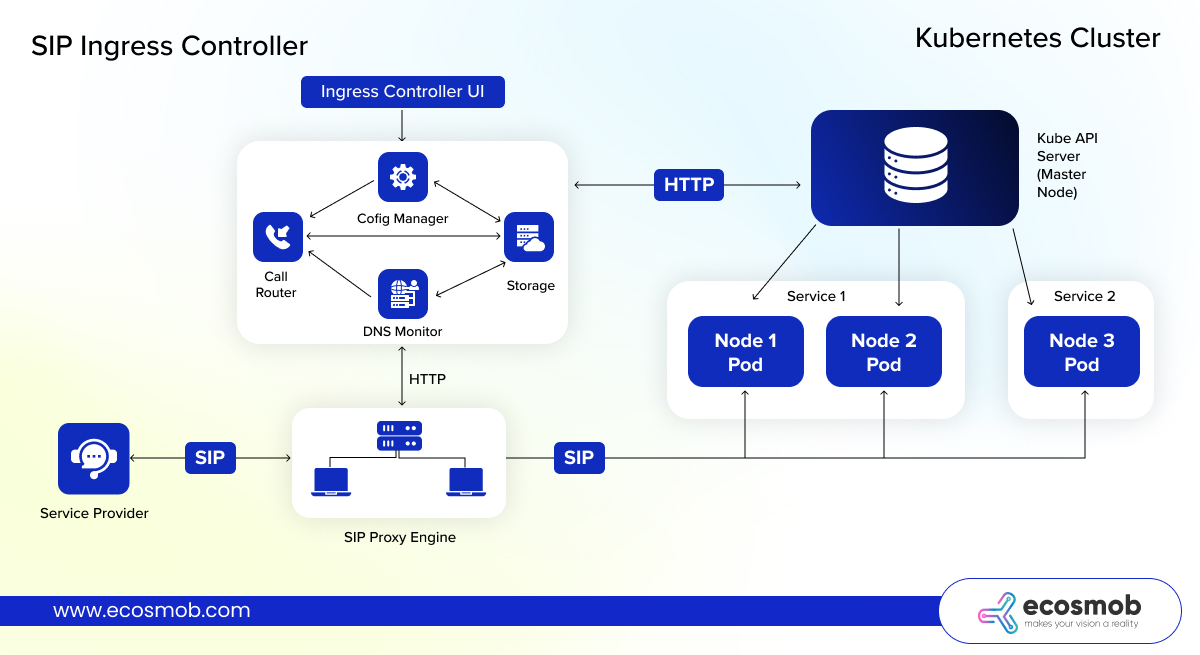
It’s the first and only cloud-native Ingress Controller built specifically for SIP traffic inside Kubernetes.
Here’s how it makes things easy for you:
✅ Fetches pod IPs in real time via K8s APIs
✅ Routes based on SIP headers, DIDs, codecs—not just host/path
✅ Supports TLS, SRTP, UDP/TCP load balancing
✅ Continuously monitors pod health and fails over without dropping calls
 And who can it benefit the most?
And who can it benefit the most?
- VoIP providers
- UCaaS platforms
- Telecom cloud deployments
- WebRTC-based apps
- Any real-time communication product that needs SIP routing at scale
If you’re handling real-time traffic, your Ingress Controller shouldn’t just “work”; it should be designed for it.
And this is the one that is.
Most companies spend months optimizing apps and containers, but overlook how traffic actually enters the cluster. That’s where the real bottlenecks begin.
An Ingress Controller isn’t just another Kubernetes add-on. It’s the layer that connects your users to your services. The right one reduces costs, simplifies deployments, and makes traffic management scale.
And if you’re running real-time communication workloads?
Ecosmob’s SIP Ingress Controller brings VoIP into the cloud-native world, with scalable, secure, and SIP-native ingress handling.
Let’s build a faster, more reliable entry point for your Kubernetes workloads. Talk to us today!
What is an Ingress Controller in Kubernetes?
An Ingress Controller manages external access to services in a Kubernetes cluster. It reads the rules defined in Ingress resources and routes incoming traffic to the correct internal services, handling path-based, host-based, and TLS-encrypted traffic.
What is the difference between Ingress and Ingress Controller?
An Ingress is a Kubernetes resource that defines traffic routing rules, like a blueprint. The Ingress Controller is the engine that makes those rules work by processing them and routing real traffic through the cluster accordingly.
Can you use multiple Ingress Controllers in one cluster?
Yes. Kubernetes supports multiple Ingress Controllers using IngressClass. Each Ingress rule can be assigned to a specific controller, allowing different types of traffic (e.g., HTTP and SIP) to be handled by different systems.
What is the best Ingress Controller for SIP or VoIP traffic?
Ecosmob’s SIP Ingress Controller is the only Kubernetes-native solution designed specifically for SIP. It supports session-aware SIP routing, load balancing, dynamic pod discovery, and failover—features that general-purpose controllers lack.
How to deploy an Ingress Controller in Kubernetes?
You can deploy most Ingress Controllers using Helm charts or kubectl manifests. The process involves creating a dedicated namespace, installing the controller, and then defining Ingress resources that it will monitor.