QUICK SUMMARY
AES 256 encryption is a highly secure method for protecting sensitive data, including VoIP recordings, from cyber threats. It ensures compliance, secures real-time communication, and enhances privacy for businesses and individuals. Learn how it works and its importance in data security.
Have You Ever Wondered How Safe Your Data Really Is?
In today’s digital world, data security is a big deal. Whether you’re protecting personal files, business data, or confidential communications, AES 256 encryption is one of the best ways to keep your information safe.
This blog will explore AES 256 encryption, explaining its relevance in data security, particularly for securing VoIP (Voice over Internet Protocol) recordings.
Also, a Research Gate report says, how implementing Advanced Encryption Standard (AES) encryption algorithms impacts key VoIP performance parameters and whether that impact falls within tolerable levels.
But what exactly is AES 256-bit encryption, and why should you use it?
Let’s break it down in simple terms.
Join the League of Businesses Using AES 256 – Protect Your Data Now!
What Is AES 256 Encryption?
First things first – define AES encryption.
AES (Advanced Encryption Standard) 256 is a symmetric encryption algorithm used to secure digital data. In simple terms, it scrambles your information in a way that only someone with the correct key can unscramble it.
And what is AES encryption algorithm?
It’s a method approved by the U.S. government and trusted by security professionals worldwide. It uses a 256-bit key, making it nearly impossible to crack through brute-force attacks. But is AES encryption secure? Absolutely! It’s the same technology used by banks, governments, and cybersecurity experts to safeguard sensitive information.
Why Is AES 256 Encryption Important?
AES 256 is widely used primarily for its high level of security. But what exactly makes it so secure? Its 256-bit key size creates 2^256 possible combinations, making brute-force attacks nearly impossible. Even the world’s most powerful supercomputer would need billions of years to crack a single AES 256 key by brute force.
Governments, financial institutions, and businesses worldwide rely on AES 256 to protect sensitive data. It’s also a trusted method for encrypting VoIP recording files, ensuring private and secure voice communications.
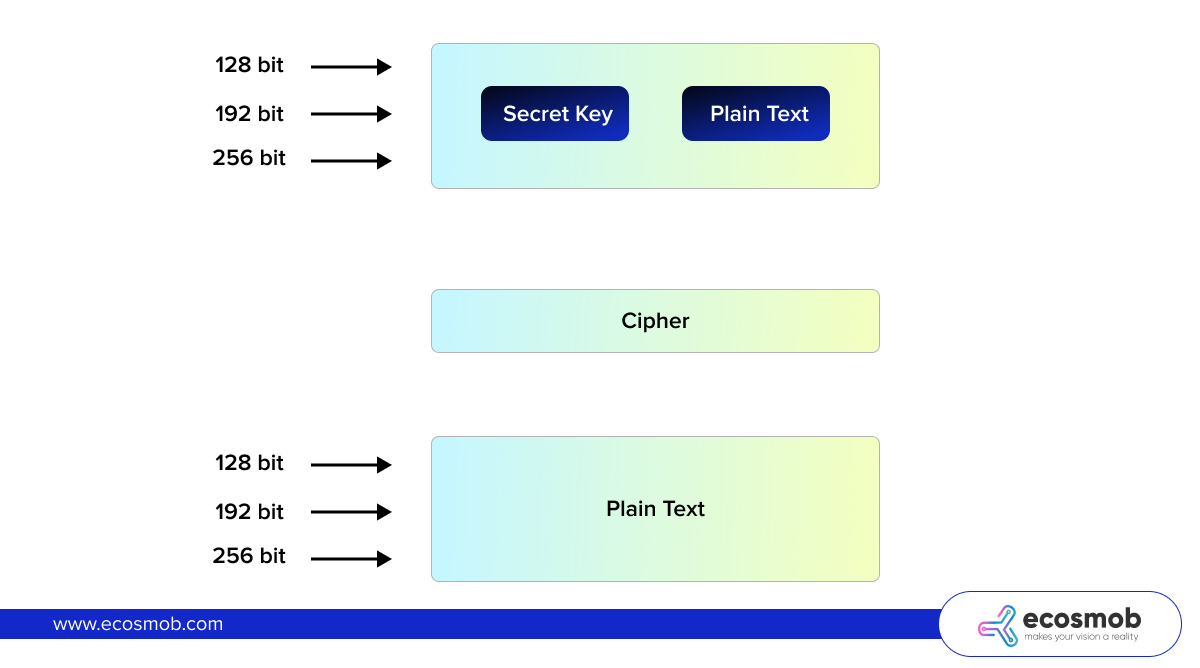
How Does AES 256 Encryption Work?
To truly understand AES 256 encryption, we need to break down the encryption process:
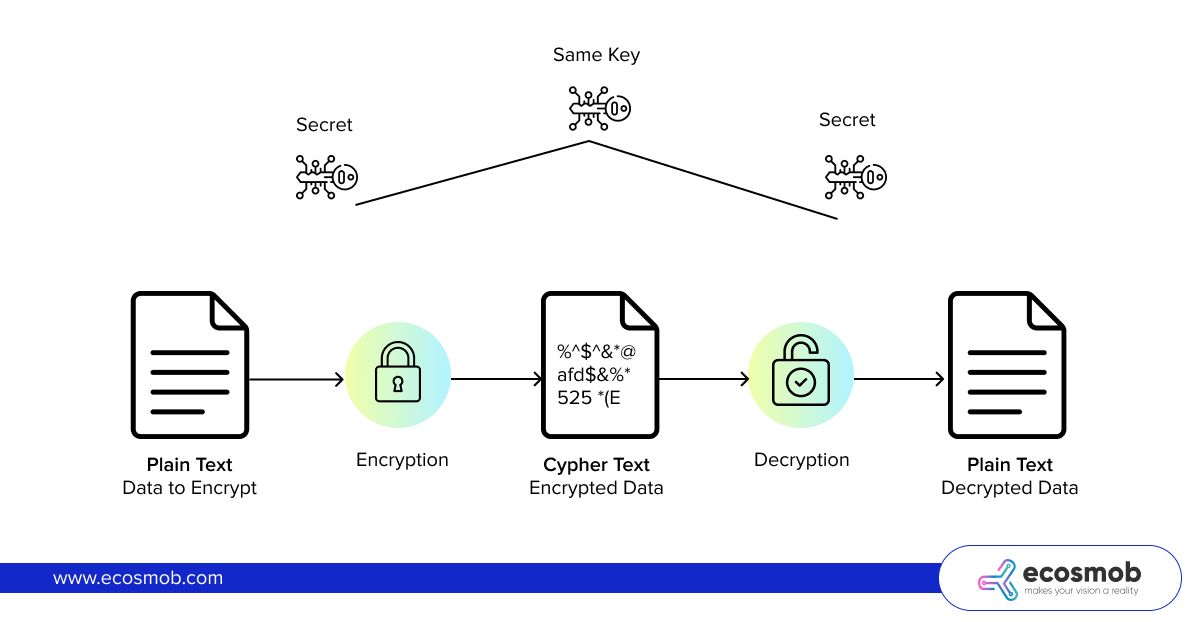
- Symmetric Key Encryption: AES 256 employs a symmetric critical encryption methodology, using the same key for encryption and decryption. It contrasts with asymmetric encryption, which relies on a public and private key pair.
- Block Cipher: AES is a block cipher that processes data in fixed-size blocks (128 bits for AES) and encrypts them one at a time. When you encrypt data using AES 256, the algorithm divides the information into blocks and applies transformations to each block.
- Rounds of Transformation: AES 256 undergoes 14 transformation processes, including substitution, permutation, and mixing. Each round strengthens the encryption by making it more resistant to attacks. The 256-bit key is used throughout these rounds to scramble the data further.
- Decryption Process: The decryption process mainly reverses encryption. The same key is required to reverse the transformation rounds and convert the data to its original, readable format.
Why Does Your Business Need AES 256 Encrypted Software?
VoIP business interactions handle massive amounts of sensitive data – customer records, financial transactions, and proprietary information. This is why business data encryption is essential. Implementing AES 256 encrypted software ensures that even if hackers intercept data, they can’t read it.
Using AES 256 encryption protects against data breaches, cyberattacks, and insider threats. Companies that prioritize advanced encryption standard 256 enhance their reputation, build customer trust, and comply with data protection laws.
Why Use AES 256 for Securing VoIP Recordings?
VoIP systems allow businesses to make voice calls online, offering significant cost savings and flexibility over traditional telephony. However, VoIP data, including call recordings, can be susceptible to eavesdropping, theft, and other forms of cyberattacks. It makes encrypting VoIP recording files crucial to ensure privacy and integrity. Here’s why AES 256 is the best choice for VoIP encryption:
- High-Level Security: VoIP calls often include sensitive data—such as private conversations, personal information, or even credit card details. AES 256 encryption secures these recordings, preventing unauthorized access.
- Compliance and Regulation: Many industries, like healthcare (HIPAA compliance) and finance (PCI DSS compliance), require strict security standards for voice communications. Using AES 256 encryption for VoIP recording ensures businesses comply with these regulations by providing solid data protection.
- Encryption of Real-Time Voice Data: VoIP transmits data in real-time, demanding an efficient encryption method that avoids adding significant latency or lag. AES 256 encrypts and decrypts data quickly, making it ideal for real-time voice communication and recording.
- Recorded Audio Security: Besides live VoIP calls, businesses often store call recordings for quality assurance, training, or legal purposes. AES 256 ensures that stored recordings remain protected from unauthorized access, even if hackers manage to penetrate storage systems.
How to Implement AES 256-Bit Encryption?
So, how to implement AES 256-bit encryption in your business or personal life? Here are a few steps:
- Use Encrypted Software – Many security applications, including VPNs, password managers, and secure cloud storage, use AES 256 encryption by default.
- Encrypt Your Devices – Enable full-disk encryption on your laptops, smartphones, and external drives.
- Secure Cloud Storage – Ensure your cloud service provider offers AES advanced encryption standard protection.
- Protect Communication – Use messaging apps with end-to-end AES 256-bit encryption technology.
- Regularly Update Security Practices – Cyber threats evolve, so always stay updated with the latest encryption methods.
Real-World Applications of AES 256 in VoIP Systems
Let’s explore some practical applications of AES 256 in securing VoIP recordings and communications:
- Encrypted Cloud Storage of Call Recordings: Many businesses use cloud storage to save VoIP recordings, allowing easy access and backup. However, cloud storage is a potential security risk if not managed properly. Applying AES 256 encryption ensures that recordings are stored securely and remain confidential, even in case of data breaches.
- Securing VoIP Transmissions over Public Networks: VoIP calls are often transmitted over public internet networks, exposing them to potential eavesdropping or interception. By using AES 256 encryption, businesses can securely transmit VoIP data over the internet without fear of being intercepted by unauthorized third parties.
- Meeting Compliance Requirements: For industries bound by strict data security regulations (e.g., healthcare, finance), AES 256 encryption can be instrumental in meeting compliance requirements for recording and storing voice data. It provides a reliable and auditable way to protect sensitive information.
Integrating AES 256 encryption into VoIP systems provides comprehensive protection across various fronts, from securely storing call recordings in the cloud to safeguarding transmissions over public networks. By implementing this encryption, businesses mitigate the risks of unauthorized access and eavesdropping and ensure adherence to strict data privacy regulations across industries. As a result, AES 256 serves as a vital tool for maintaining confidentiality, compliance, and the overall integrity of voice data in an increasingly interconnected and security-focused environment.
The Future of AES 256 and VoIP Security
While AES 256 remains the gold standard for encryption, evolving threats require continuous vigilance. As quantum computing and advanced hacking techniques emerge, the need for robust encryption will only grow. Here are some future trends to watch for:
- Post-Quantum Cryptography: Quantum computing threatens current encryption algorithms, including AES 256. Researchers are developing post-quantum cryptographic algorithms that can withstand quantum attacks, ensuring that future VoIP communications remain secure.
- Integrated Security Solutions: Businesses increasingly seek integrated security solutions combining VoIP encryption, secure storage, and key management into a single platform. This holistic approach will make it easier for companies to implement AES 256 and other security measures seamlessly.
- AI-Powered Security Threat Detection: Artificial intelligence detects security threats and vulnerabilities in VoIP systems. By combining AI-based threat detection with AES 256 encryption, businesses can proactively protect voice communications and call recordings from potential cyberattacks.
 The future of AES 256 and VoIP security is evolving to address emerging challenges like quantum computing and sophisticated cyberattacks. While AES 256 remains a robust encryption standard, ongoing advancements in security are vital to maintaining data protection. As post-quantum cryptography develops, businesses will be better equipped to defend against potential quantum threats. Additionally, the trend towards integrated security solutions will simplify combining encryption, storage, and critical management, enhancing overall protection. With AI-powered threat detection further bolstering security measures, combining these technologies with AES 256 encryption will provide a proactive and comprehensive defense against evolving vulnerabilities in voice communications.
The future of AES 256 and VoIP security is evolving to address emerging challenges like quantum computing and sophisticated cyberattacks. While AES 256 remains a robust encryption standard, ongoing advancements in security are vital to maintaining data protection. As post-quantum cryptography develops, businesses will be better equipped to defend against potential quantum threats. Additionally, the trend towards integrated security solutions will simplify combining encryption, storage, and critical management, enhancing overall protection. With AI-powered threat detection further bolstering security measures, combining these technologies with AES 256 encryption will provide a proactive and comprehensive defense against evolving vulnerabilities in voice communications.
Why is AES 256 Encryption the Best Choice?
We’ve answered the questions –
- what is AES 256 encryption,
- how does encryption work, and
- is AES encryption secure?
The summary?
AES 256-bit encryption technology is the gold standard for protecting data.
For businesses dealing with VoIP recordings, AES 256 meets stringent compliance regulations and offers peace of mind, knowing that a secure and reliable encryption standard protects your data. From encrypting real-time voice transmissions to safeguarding stored call recordings, AES 256 is a powerful tool for ensuring data security in today’s interconnected world.
Now is the time to switch if you still need to start using AES 256 encryption to secure your VoIP data. Ecosmob Technologies specializes in implementing robust encryption solutions tailored to your business needs. With the right encryption strategy and tools provided by Ecosmob, you can protect your sensitive information, meet compliance requirements, and maintain the integrity of your communications seamlessly and effectively.
Secure Your Data Like a Pro – Switch to AES 256 Now!
FAQs
What is AES 256 encryption, and why is it so widely used?
AES 256 is a type of Advanced Encryption Standard (AES) that uses a 256-bit encryption key, making it one of the most secure encryption methods available. Its widespread use is due to its high level of security, efficiency, and ability to protect sensitive data across various applications, including VoIP communications, government agencies, financial institutions, and cloud storage.
How secure is AES 256 encryption compared to other encryption methods?
AES 256 encryption is extremely secure due to its large key size, which makes it highly resistant to brute-force attacks and other types of cryptographic exploits. Thanks to its more complex key structure and higher number of transformation rounds, it is considered more secure than its predecessors, like DES (Data Encryption Standard) and even the AES 128 and AES 192 versions.
Why is AES 256 encryption recommended for VoIP recordings?
VoIP recordings often contain sensitive information such as business conversations, personal data, and confidential communication. AES 256 encryption protects these recordings from eavesdropping, theft, and cyberattacks during real-time transmission and storage, ensuring compliance with regulations and safeguarding data privacy.
How can I implement AES 256 encryption for my business's VoIP systems?
To implement AES 256 encryption, you'll need a VoIP system or communication platform that supports this encryption standard. It typically involves securing end-to-end encryption for real-time voice data and encrypting stored call recordings. Partnering with a technology provider like Ecosmob Technologies can help you set up an AES 256-secured system with proper key management, compliance checks, and data privacy protocols.
Is AES 256 encryption future-proof?
AES 256 provides security against current threats, but quantum computing could challenge all modern encryption standards. Researchers are developing post-quantum cryptography algorithms to protect data against these emerging technologies. AES 256 is a robust and secure choice for data and VoIP encryption.